Ubuntu Core 20 (UC20) is built on the foundations of Ubuntu 20.04 LTS (Focal Fossa). It’s the next generation of Ubuntu for embedded devices.
New features for this release include:
- Raspberry Pi support (both ARMv7 and ARM v8)
- Full-disk encryption via TPM integration
Currently x86-only with ARM to follow. TPM integration works with existing CA - A new recovery and reinstall mode
- Recovery mode menu and chooser
- Initial MAAS & cloud-init support
See below for an overview of UC20’s features and see Ubuntu Core 20 for more comprehensive documentation of these features within the wider Ubuntu Core platform.
Latest image downloads
Download the latest UC20 images from:
http://cdimage.ubuntu.com/ubuntu-core/20/stable/current/
Recovery mode chooser
To access the recovery chooser, reset or start up UC20 while holding the 1 key.
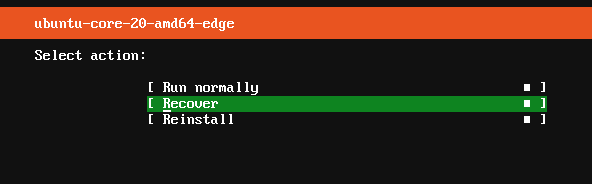
The 1 key needs to be held until the initial boot process completes, after which you’ll be presented first with the system selection menu followed by the following recovery options:
- Run normally: Continue with the boot process.
- Recover: reboot into recovery mode and log into the system using prior credentials to recover your data, either via SSH or locally after setting up a password for the user.
- Reinstall: initialise the device from the listed system version image. All existing user data on the device will be removed.
See Recovery modes for further details.
Model definition
The model definition has been expanded for UC20 devices to include several new options, most notably grade and snaps (see Custom images for details on building images).
`grade:`
Sets the constraints for the device. It can be one of the following:
-
dangerous: relax some of the constraints here (mandatory snap id for example), and should allow for the use of unasserted snaps, devmode snaps, or the presence of extra snaps in the recovery system. -
signed(default): no unasserted (unsigned) snaps or snaps not mentioned in the model can appear or be used in the recovery system. -
secured: same properties as signed plus it is mandatory for the device to use full disk encryption and secure boot.
`snaps:`
A new header to control which snaps comprise the device setup. It consists of the following keywords and mappings:
-
name(mandatory): name of the snap. Cross-checked at image build time but ignored later -
type(mandatory): type of the snap, needs to be either:base|gadget|kernel|app|core. app is the default -
id(optional): id of the snap if assigned by a store. Must be omitted for local snaps. -
modes(optional): a list with UC20 modes (verbs, “run”) or mode aliases (“ephemeral”, covers all recovery/tmpfs modes) for which the snap needs to be installed. Default is [run], should not be used for typeskernel|gadgetand for the snap indicated by the “base” header -
presence(optional): set to mark a snap whose absence will not fail installation or recovery. Can be optional or required of which required is the default -
default-channel(optional): initial tracking channel for the snap, default is “latest/stable”
The appearance of the snaps keyword prohibits the use of gadget, kernel and required-snaps as the same information and more is conveyed through the snaps header.
Example UC20 Model definition
The following is an example model definition for amd64:
type: model
authority-id: canonical
series: 16
brand-id: canonical
model: ubuntu-core-20-amd64-beta
architecture: amd64
base: core20
grade: signed
snaps:
-
default-channel: 20/beta
id: UqFziVZDHLSyO3TqSWgNBoAdHbLI4dAH
name: pc
type: gadget
-
default-channel: 20/beta
id: pYVQrBcKmBa0mZ4CCN7ExT6jH8rY1hza
name: pc-kernel
type: kernel
-
default-channel: latest/beta
id: DLqre5XGLbDqg9jPtiAhRRjDuPVa5X1q
name: core20
type: base
-
default-channel: latest/beta
id: PMrrV4ml8uWuEUDBT8dSGnKUYbevVhc4
name: snapd
type: snapd
timestamp: 2020-01-13T15:47:00.0Z
sign-key-sha3-384:
Testing UC20
The easiest way to test the latest UC20 release is to download the latest image and either write the image to a USB storage device, and test the build on real hardware, or use the image with a virtual machine.
If your hardware supports TPM, and has UEFI Secure Boot enabled, UC20 will use these to deploy a fully encrypted system. When redeploying to the same device, the TPM will need to be cleared.
To test UC20 with QEMU (https://www.qemu.org/), first install the OVMF package (eg. sudo apt install ovmf) then run the following command to boot a UC20 image (renamed pc.img) within a virtual machine:
sudo qemu-system-x86_64 -smp 2 -m 2048 \
-net nic,model=virtio -net user,hostfwd=tcp::8022-:22 \
-drive file=/usr/share/OVMF/OVMF_CODE.fd,if=pflash,format=raw,unit=0,readonly=on \
-drive file=pc.img,cache=none,format=raw,id=disk1,if=none \
-device virtio-blk-pci,drive=disk1,bootindex=1 -machine accel=kvm
Older OVMF packages can cause QEMU boot problems. Either build them manually, or consider extracting the files from a more recent package. OVMF for Ubuntu 20.04 LTS (Focal Fossa)](https://releases.ubuntu.com/20.04/) is known to work.
With a successful boot, Ubuntu Core initialisation will ask for both networking parameters and an Ubuntu One account (see https://snapcraft.io/account).
When the initialisation process has finished, and rebooted, you can SSH to the device using either the physical device network address, or localhost port 8022 for the above QEMU example command:
$ ssh <username>@localhost -p 8022