As announced in Ubuntu Desktop 25.10 - The Questing Quokka Roadmap post, one of the feature we want to develop on this cycle is our TPM/FDE implementation for Ubuntu 25.10.
TPM/FDE in a nutshell
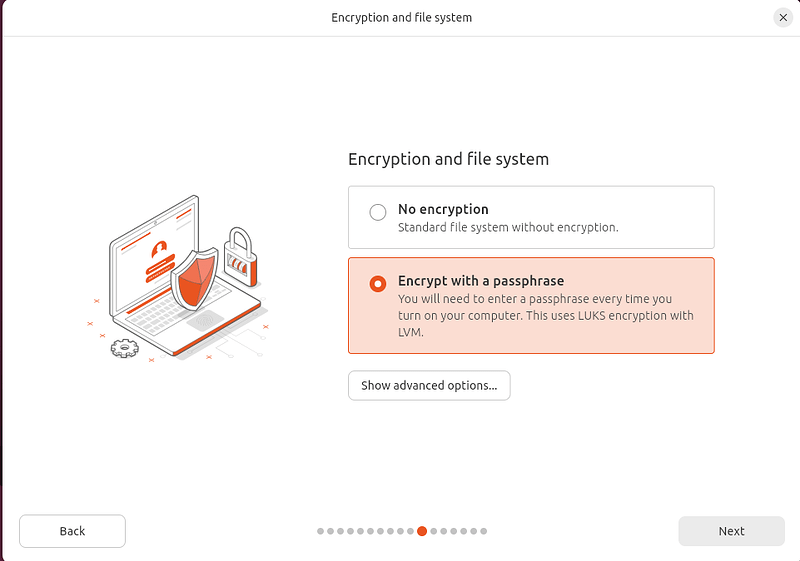
So, first, what is this about? FDE stands for Full Disk Encryption, providing you a way to ensure that all your content on disk is encrypted and inaccessible at rest. We offer a traditional FDE option for many years in Ubuntu and it’s available during installation:
You can then define a passphrase to unlock the disk, before the system boots.
So, what’s different here? TPM, or Trusted Platform Module is a chip (it can be implemented in pure software too) that you find in most modern computing units. This platform helps to ensure the integrity of a platform during boot time. It means that it will measure most of the software and firmware that are running before the operating system (Ubuntu here) starts, alongside some critical components of the early boot of it, and will only allow unlock the encrypted disk under the conditions they assert a given system state. It needs tight cooperation with the operating system to secure this functionality. With all this, you can ensure that your hardware and early firmware/software are the ones you trusted when you did your installation and have not been tampered with afterwards. It also means that the disk will not be readable on another device or if you swap parts of your hardware (but you can still use the recovery key in that case, more on that later).
Please note that this feature is considered experimental on Ubuntu 25.10. This is clearly something you shouldn’t (yet) install on a production environment. However, you can try and play with it on any system you know you can recover your data on. We’ll consider you are now warned about what to do wisely :). Our goal is to progress, collect feedback and work on this set of capabilities during the following development cycles.
Let’s now illustrate the main use cases and features that will be available in Ubuntu 25.10. Not all of them fully landed yet as questing is still in development, so stay tuned!
Better TPM safety and configuration detection.
First thing to note is that we now have more fine-grained checks to ensure that enabling TPM/FDE can be done in a safe and controlled environment. Our goal is to remove a false sense of security due to misconfiguration of the hardware or to fail post-installation.
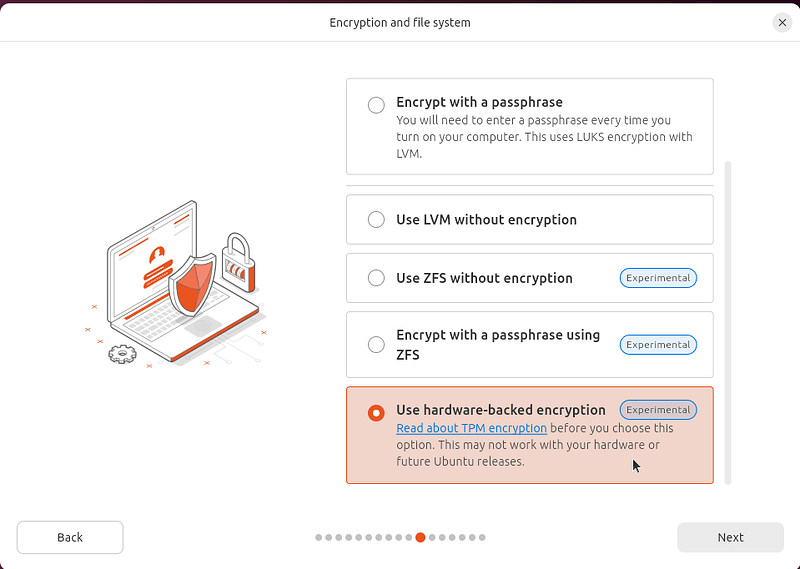
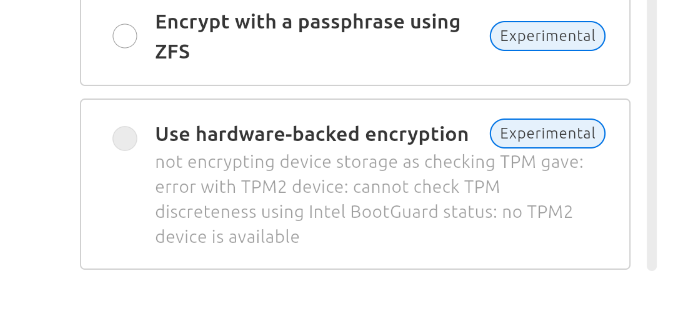
Under Advanced options on the Encryption and file system screen, you can only select the TPM installation if we detect that your system is ok to run with it (new enough version of the TPM, no known unpatched vulnerabilities, proper configuration…). Under those conditions, you will be able to choose the Use hardware-backed encryption option:
If we detect that anything would prevent this installation to be successful in a trusted manner, we will then print (sometimes a technical) warning:
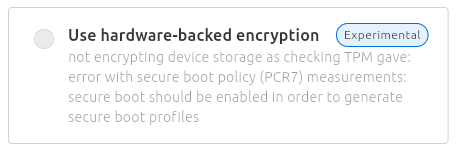
Or another example:
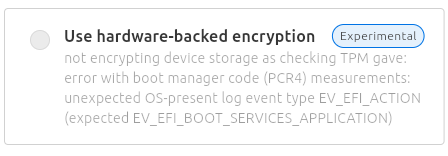
In the future (post 25.10), we will expand those with Actions that either provide a recommendation of something that has to be done manually (like enabling Secure Boot) or by something that could be performed directly by snapd, like clearing out the TPM, after you gave your consent.
What does it mean for our users who tried TPM/FDE before? It may be that previously allowed installation configurations are more restricted now as deemed not to be safe enough. This detection can have some false positives, as it’s heavily hardware dependent and we need to know what it gives us in the real field (and not only from the TPM specifications which might be partially implemented by the hardware manufacturer).
We plan to do a call for testing with some extra tools for volunteers to run on their setup so that we can collect feedback of successful configuration and what is preventing other types of installation. Subscribe to this thread or lurk our Ubuntu discourse near the 25.10 release next October for such a call if you are interested to help with that effort! That will be invaluable feedback, helping us getting an understanding of the hardware configuration available in the wild and be confident when we will ship it as a stable feature!
Recovery key
When we install a TPM/FDE system, we also generate a recovery key. What is this for?
The recovery key is used to bypass the TPM completely (you can think of a derived LUKS passphrase, for the more technophils). This key can be useful in many cases:
- When you upgrade some of your machine firmwares (more on that later)
- When you change parts of your critical hardware changing the measurements
- When you don’t remember your passphrase
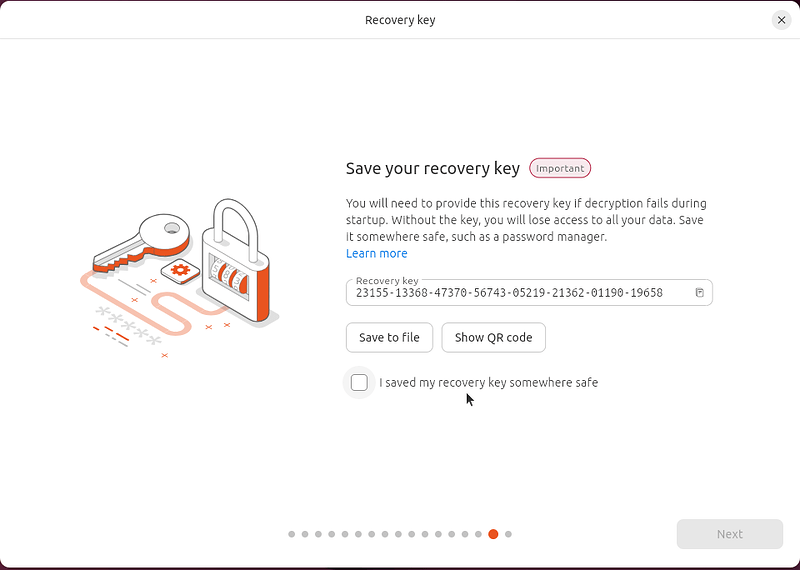
So it’s “key” to save it somewhere. To hilight its imporance, on the last installer screen, you will get it displayed front and center, telling you to either write it somewhere on real paper, save it in file outside of the live system (we have some checks to prevent you doing that and shooting yourself in your foot ;)), or display it as a QR code.
Once you acknowledge having done that, you will be able to reboot to your shiny new hardware-backed FDE installation!
Passphrases
However, there is probably another TPM/FDE related option you noticed: passphrase support.
With traditional TPM usage, the disk is unlocked when the TPM state is the expected one, meaning that your hardware and software is trusted. This is a transparent process (no additional user input needed) with a huge gain in terms of security.
Optionally, you can opt in to use a passphrase in addition to the TPM. Note that this is different from traditional Full Disk Encryption without TPM: the disk will unlock only if the TPM state is the expected one and after you provide your passphrase! You thus have a double protection (the TPM confirms the state of the system, but only you, knowing your passphrase can fully unlock it).
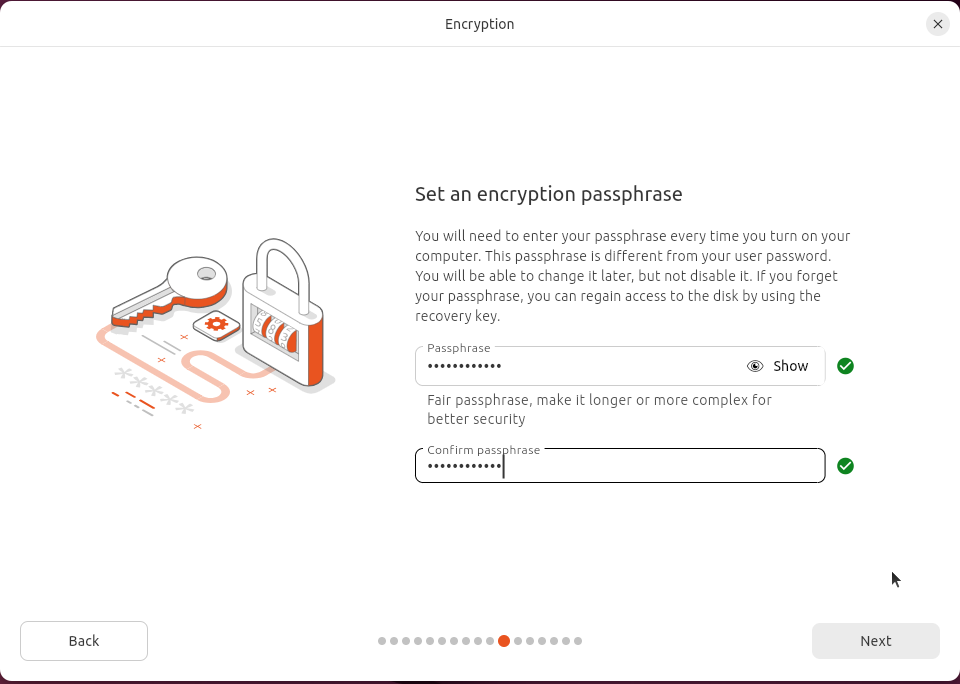
This can be setup during the installation and you will informed of the strength of your passphrase:
This passphrase will be prompted every time you boot your machine:
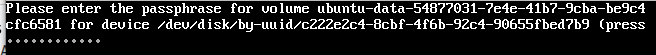
If you don’t remember the passphrase, you can always use the recovery key that you have safely written down and kept secure (you did write it, right? :)).
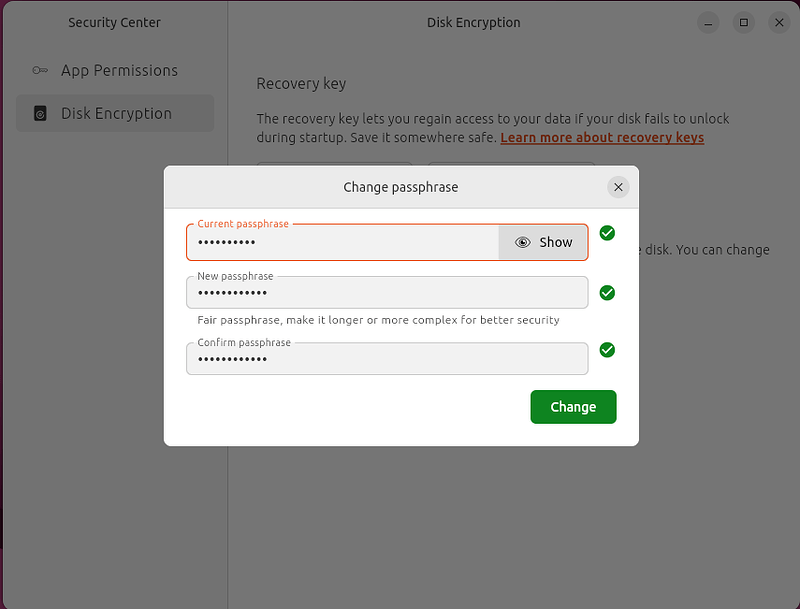
You can change your passphrase in the new Security Center panel dedicated to TPM/FDE. It provides a similar user experience than the installer. For the time being, you have to enter your previous passphrase to change it, but an option with admin support (asking for the system admin password, but not the previous passphrase) will be soon available, but potentially, post 25.10.
Firmware and hardware updates
Another point is the advanced integration with our firmware updates UI. For updates like the DBX (secure boot signatures database) updates, where snapd can predict the next TPM state, this is fully transparent. You will upgrade, reboot and won’t be asked for anything else.
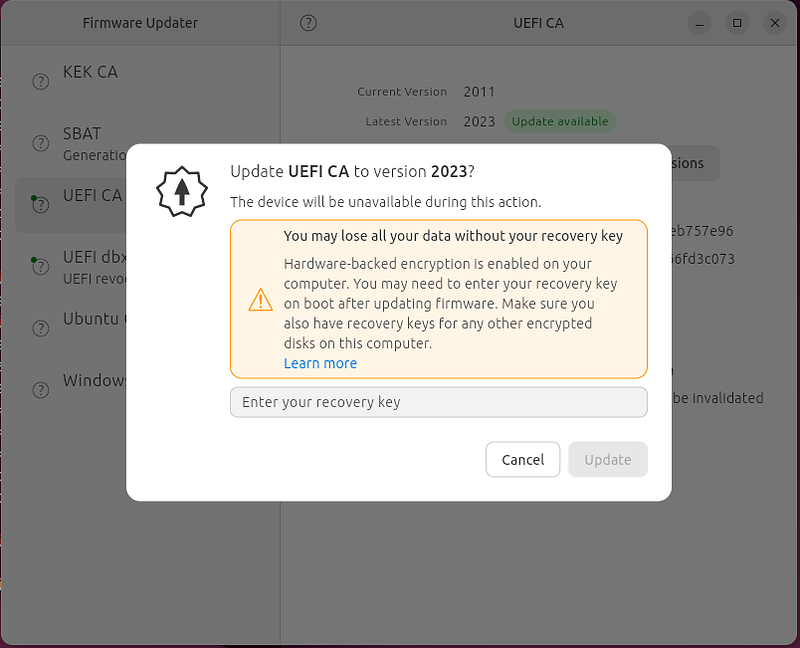
However, for other kinds of updates like new firmwares or hardware replacement, we can’t know in advance what will be the new state of TPM on boot. As such, we will request you enter the recovery key to “stamp” the new state as valid and trusted. Then, this becomes the new reference and any followup reboots won’t ask for your recovery key anymore and will use the new TPM state as a reference.
Of course, you should be suspicious if the recovery key is prompted at boot without you being aware of any firmware update or hardware change. This feature is here to help you.
As again we want to protect our users to not end up in a situation where they update some firmware without knowing their recovery key. This would mean otherwise that they can’t reboot their machine as it will prompt for the recovery key they don’t have handy. So, we double check by asking for it before applying any update in the firmware updater! Of course, this additional verification is only done when required, so not when we can predict the next TPM state like on DBX update.
Another use case is firmware upgrade impacting other TPM-related installation even if your Ubuntu installation is not TPM/FDE enabled. For instance, if you have another operating system like Windows with BitLocker installed on your machine, and you update some firmware or DBX from your Ubuntu system, Windows will prompt you for your BitLocker recovery key on next boot. We display a warning before letting the user upgrade their firmware if we detect such a situation.
Recovery key replacement
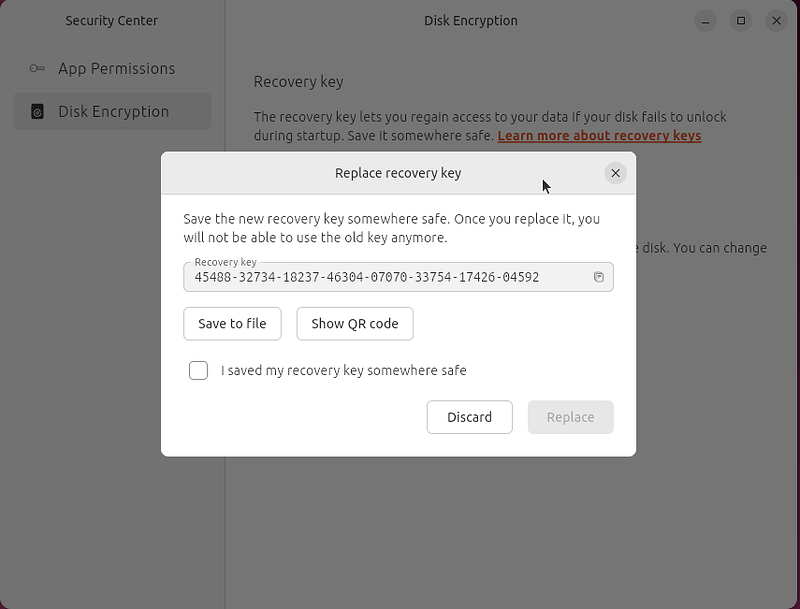
Now that you understand that your recovery key is very important to your TPM/FDE system, what happens if your system booted successfully, but you don’t remember or lost your recovery key?
Fortunately, we have a solution for you: the security center offers you to regenerate a new one if you are an administrator on your system. Keep this new one safe and secure. ![]()
Extensive end to end tests
We are building an extensive end to end testsuite running on both virtual and physical machines (as it should be clear now that the TPM is highly hardware-dependent) to ensure all those user stories are covered. We understand our responsibility as bugs could potentially lock you out of your data and we don’t want to corner you in that situation. You always have your recovery key anyway to bypass the TPM and recover them, so for the last time, keep it safely written and protected!
Documentation
The documentation is currently being updated to integrate TPM/FDE information with all the former points. We aim to have a good technical and a more user oriented ones when we will release it as a stable feature in our general Ubuntu documentation.
What about binary drivers, like nvidia?
The support for such drivers is still in progress, relying on a feature named snap components. When you install a TPM/FDE system, the kernel itself is in a snap and this is completely transparent to the end user! However, this creates unique challenges to expose the drivers to the rest of the system. Work on this is still in progress in that area and we hope to have something available by the end of the cycle.
In summary
Those are the most prominent features that should be available in the incoming Ubuntu 25.10 release. A lot of more fine-grained features have not been detailed here, like TPM state report in the security center, different levels of entropy detection for your chosen passphrase…
Keep in mind that everything described above are currently landing in questing and are not yet fully functional out of the box. For instance, as of today, some manual snap connections are still needed and some polkit files need a manual copy until the next snapd release. We will make the call for testing closer to the 25.10 release.
A lot still needs to be done, like a better UI on boot for asking passphrase/recovery key interchangeably, PIN support, administrative tooling, help the user to enable and reconfigure their system to be TPM/FDE enabled… But the basics that are hitting Ubuntu 25.10 are solid and implemented.
I hope this gives you a better understanding of where we are going with TPM FDE on Ubuntu and gets you equally excited about it as we are!